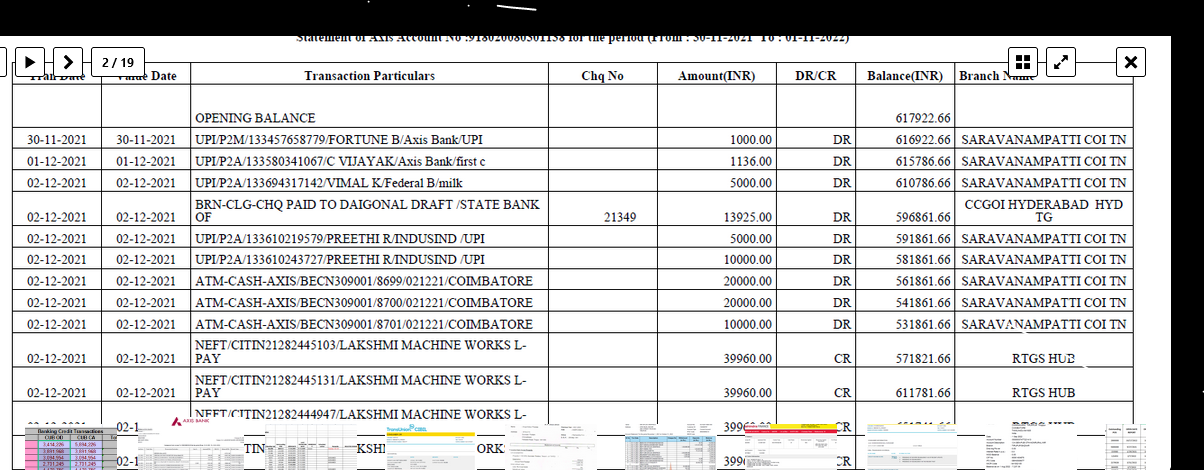
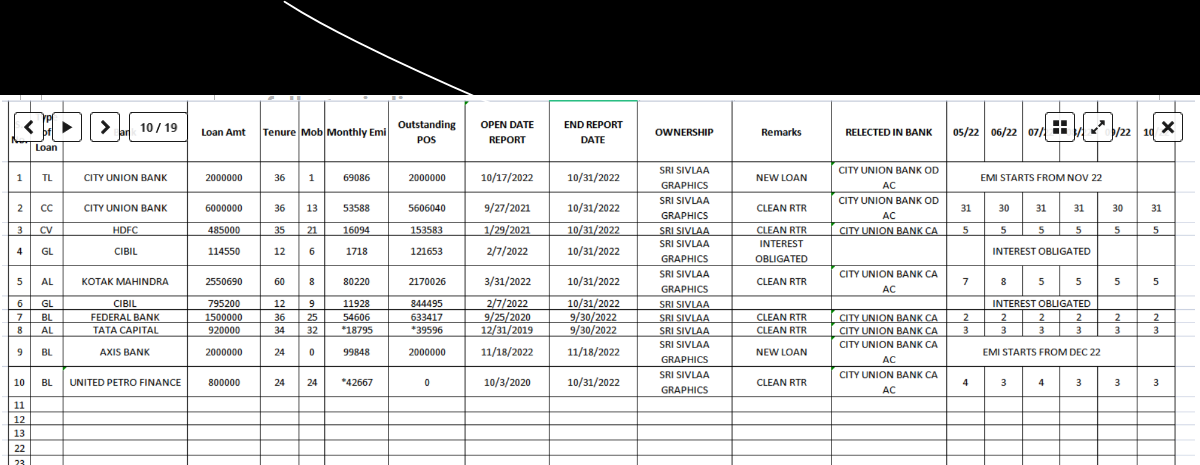
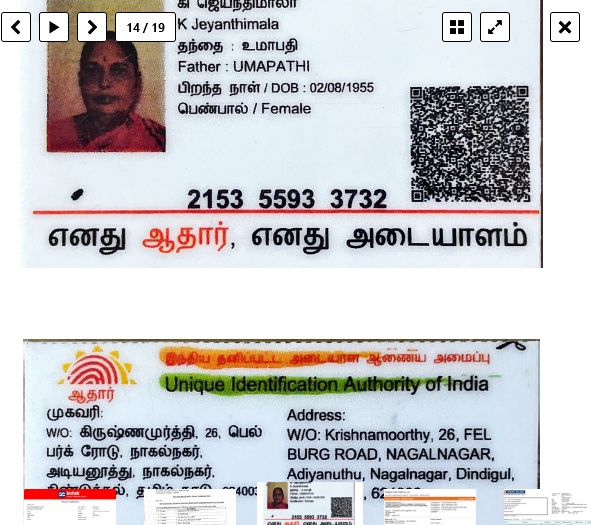
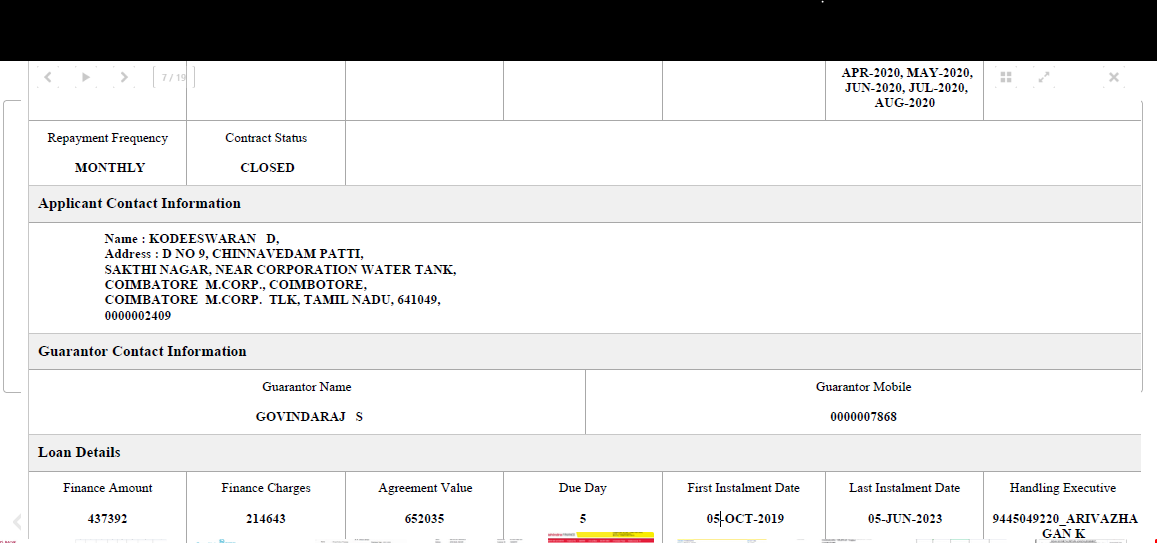
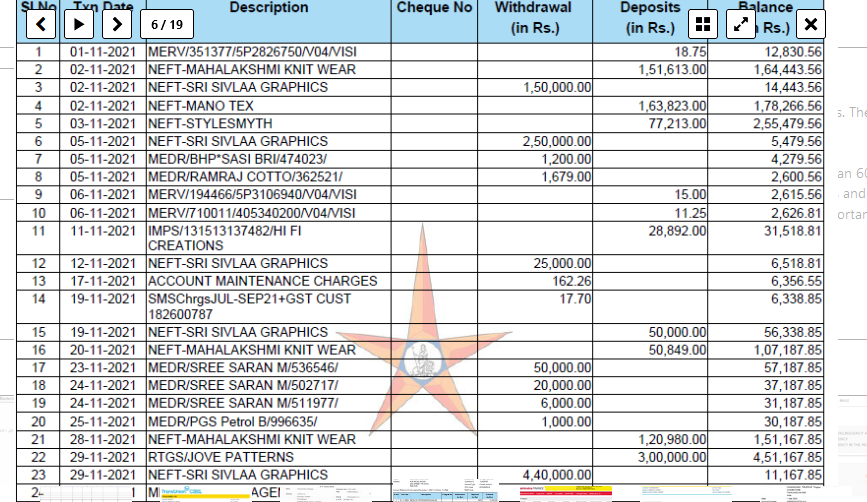
More than 600 GB of critical data from Fullerton India has been published on the dark web by the Lockbit 3.0 ransomware group on their blog of the same name on May 3, 2023. The hackers were demanding a ransom amount of Rs. 24 crore and had given Fullerton India almost a week’s time to negotiate. Apparently, the company refused to negotiate with the hackers.
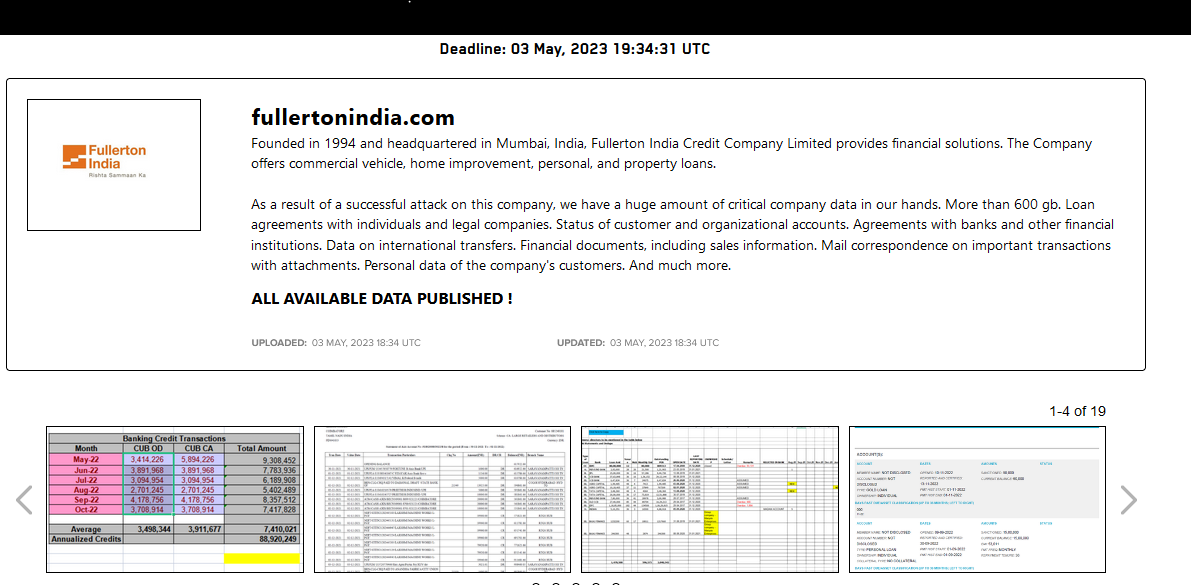
On April 24, the major NBFC had stopped services for a short time after the data breach was detected. Fullerton India later shared an official statement with ETCISO, saying the company had begun resuming services for its customers and had addressed the malware incident and informed relevant stakeholders of a cyber incident, after which operated offline as a “precautionary measure”. Fullerton India he added in his statement that the company was working with the world’s top experts to “significantly improve its security environment for future expansion.” It works in the retail and rural segments and offers secured and unsecured loans to companies and individuals.
Lockbitransom demands
LockBit 3.0 had asked $29,999.99 or Rs. 24 million ransom to destroy the breached data. Since the darkweb blog operates on a ransomware-as-a-service model, it also offers an option to the company’s competitors or anyone interested to purchase and download the data for the aforementioned amount. Before, the countdown timer was “in the green” as the company had time to respond. After a certain amount of time, the timer became “published”.
Lockbit generally allows a period of 10 days for the organization to pay from the day the data breach is announced on its blog. This payment period can also be extended by paying a specified amount within a one-day period (for example, in the current case, $1,000 had to be paid to extend the “Timer” by 24 hours). Once the deadline had passed, the data was released on May 3.
LockBit 3.0: A Prolific Ransomware Group in an Age of Recruiting
Fullerton India is not the only victim of LockBit 3.0 in the latest wave of thefts. A report of cybersecurity firm Reliaquest says LockBit 2.0 was the most active group in the third quarter of 2021 with a total of 203 victims. According to the U.S. Cyber security Infrastructure and Security Agency (CISA), the latest version, LockBit 3.0, also known as “LockBit Black”, is more modular and evasive than its previous versions.
Posted on May 8, 2023 at 09:14 IST
Join the community of more than 2 million industry professionals
Subscribe to our newsletter to receive the latest statistics and analysis.
Download the ETCIO app
Get real-time updates Save your favorite articles
![]()
![]()
Scan to download the app

[ad_2]
Source link